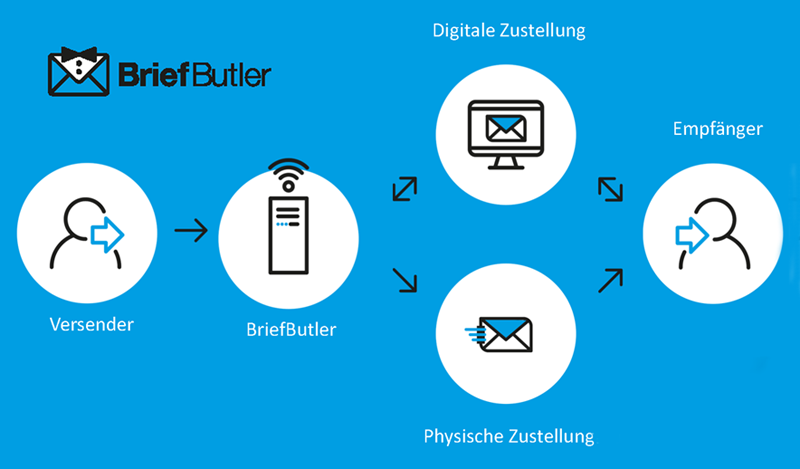
What digital skills will we need in the future? What are digital business models?
Companies and organisations are making progress with digital transformation at different speeds. While some limit themselves to digitalising existing business processes, others proactively develop digital concepts and business models. The decisive factor for success in digitalisation is the so-called „digital maturity level“. This is a scientifically based 360-degree instrument that is used to analyse all the factors that are important for change.
Digitisation explained simply
Over the past 20 years or so, various digital technologies (mobile internet, artificial intelligence, internet of things, etc.) have been drastically developed and have made the leap from expert applications to everyday life. Just as the innovation of the steam engine has changed society, so too has the digital transformation.
Digitalisation is driven by technology. Digital innovations are created on the basis of the digital technologies developed: New use cases driven by existing companies and start-ups with venture capital. This leads to different speeds. While public administration, for example, often only accepts paper documents and works with files, markets are changing much faster. All sectors are now affected by digitalisation. Digitalisation is also influencing the future of the finance and insurance industry. New forms are only possible thanks to digitalisation technologies, which will continue to spread in the future.
Digitalisation is changing the future of traditional professions. In future, doctors will be increasingly supported by e‑health applications, especially in diagnostics. Legal services (currently primarily provided by lawyers) will be supplemented or replaced by digital services from the legal tech sector. And the term Insuretech has already been established.
In the future, digitalisation will make new demands on schools, education and training in all areas. It is the task of business, associations and politics to prepare society for the coming changes.
Digitalisation and companies
Digitalisation has an impact on companies of all sizes. On the one hand, companies are using digital technologies to digitalise their business processes, i.e. for process optimisation and process innovation. This is also being driven by digital transformation and in some cases realised by start-ups. The challenge for companies in digitalisation is to identify new customer needs that arise due to the growing spread of digital services and apps.
The so-called „digital natives“ have also created new target groups. Companies often need different marketing and sales strategies to increase their customer focus on these target groups. Action must be adapted in order to be successful in the digital transformation Companies must address the question: How do we want to reach customers tomorrow? What role do new trends play? How do we deal with the increasingly individualised needs of our customers?
Development of digital workflows and processes: Saying goodbye to paper files by introducing processes and workflows in the company, some of which need to be radically rethought as a result of digitalisation, such as the handling of data that is generated within the company, in connection with a company’s activities and by customers. Data can be used to develop new services and business models. Digitalisation presents us all with the challenge of permanently changing and adapting. Competitive advantages from the past only exist to a limited extent. To achieve this, companies need to drive digital transformation within the organisation and increase their digital readiness.