A Customer portal for business and private
Send premium invoices and other documents easily, electronically and securely.
Brokerweb is a customer portal similar to e‑banking. It provides customers with all the latest important information at all times, delivers documents and offers various services such as enquiries, claims notifications and more. In contrast to e‑mail correspondence, the exchange of data and documents is secure and complies with current data protection regulations.
In addition to these technical features, the individuality of the broker and thus customer loyalty has also been increased. To this end, BrokerWeb can be configured at various levels. Rapid contact with the responsible advisor is just as important as simple handling for the customer. Various clients can be mapped in BrokerWeb by WMC. In addition, different rights can be assigned to different people. With chat function since spring 2024.
The portal is responsive and can therefore be used on all end devices such as PC, Mac, tablet or smartphone. Its ease of use makes it a practical tool for both business and private customers when it comes to insurance and broker services. It is also very important that the requirements of the new Data Protection Act (nDSG), which came into force on 1 September 2023, are met.
Login: demo-de
Password: demo-de
Features
Data protection
– nDSG requirements are fulfilled.
Home page (Figure 1)
- Main navigation
- Quick selection configurable
- Supervisor contact details
- Information from the broker
- User profile settings
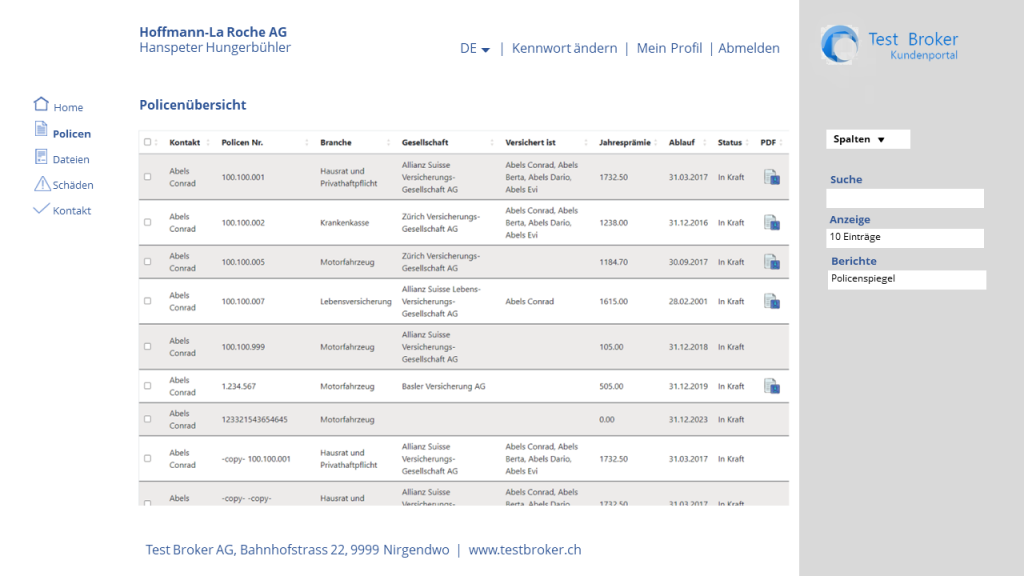
Policy overview (Figure 2)
- Global or by sector
- Search, selections
- Print
- Documents
- Jump address to policy details
- Jump address to damage
- Jump address to further files
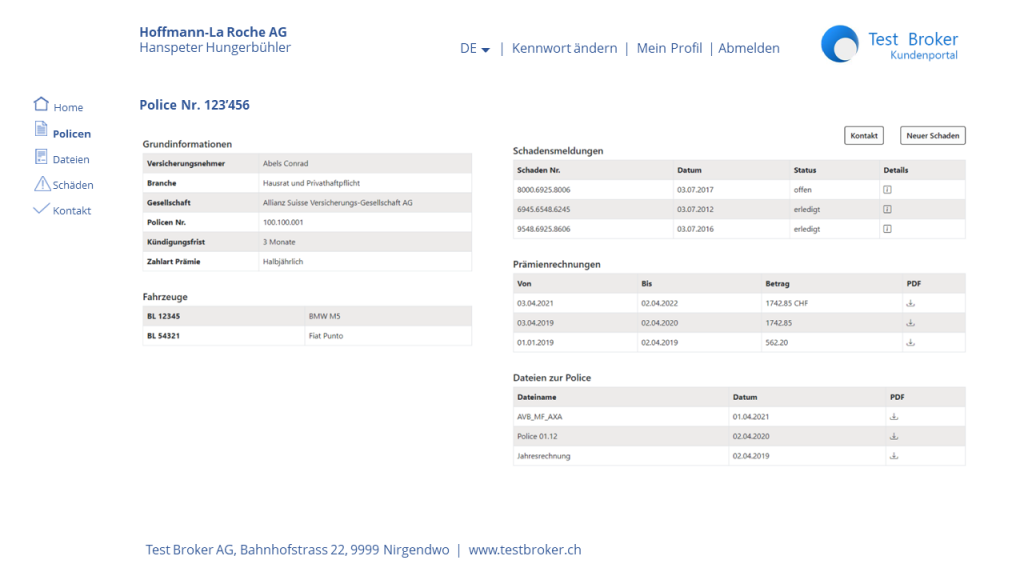
Policy details (Figure 3)
- All information about the policy
- including documents
- Damage overview
- Overview of invoices
- Overview of documents, files
…and many other functions