Legal basis
The implementation of risk management for SME companies makes a significant contribution to the fulfilment of the legal requirement pursuant to Art. 716a of the Swiss Code of Obligations, according to which the Board of Directors, as the company’s top management, is obliged to organise the accounting system, prepare the annual report, carry out financial controls and manage the company.
Principles of risk assessment
From a practical point of view, it is important for the Business Judgement Rule* to be invoked that these formalities are properly observed, that the interests of the company are taken into account in the event of conflicts of interest and that the opportunities and risks of a business decision are documented. If all requirements are met, the Business Judgement Rule can provide a defence against allegations of a breach of duty.
Opportunities for the broker
Support your customers
The four objectives of risk management:
- Taking responsibility
- Optimise adhesion
- Protect reputation
- Maximise profits
Contact
La Bella Consulting AG
Old Winterthurerstrasse 14A
8304 Wallisellen
www.riskaware.ch
Information and counselling
Marco La Bella
Managing Partner, Co-Founder
Phone 076 355 55 13
marco.labella@labella.ch
Silvia Kljajic-Canale
Senior Consultant
Phone 079 585 14 72
silvia.kljajic@labella.ch
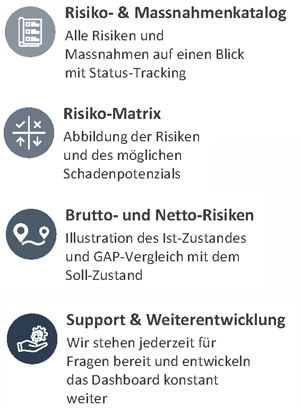
Online Risk Dashboard
risks can be viewed at any time and
can be any can be filtered.